7 phishing campaigns for corporate communication to share with stakeholders
By Bre ChamleySeptember 7, 2023
Protect your company’s data from these seven different types of phishing campaigns online.
 When it comes to cybersecurity, companies and corporate communications professionals need to know about the different types of phishing campaigns that might compromise your company's data.
When it comes to cybersecurity, companies and corporate communications professionals need to know about the different types of phishing campaigns that might compromise your company's data.
Some of these phishing campaigns might be new to you. You may have experienced them personally or professionally. Either way, education is the first step to protecting you, your company, your employees, your organization’s brand, and your reputation. The second step is active and ongoing cybersecurity communication. In the modern era, every public relations and corporate communication practitioner has the responsibility of leading the charge for cybersecurity communication.
Audio: Listen to this article.
We are a trusted public relations advisor to cybersecurity companies and organizations seeking helpful expert guidance on corporate communication before, during, and after a cyber attack.
The following is a list of phishing campaigns you need to be aware of:
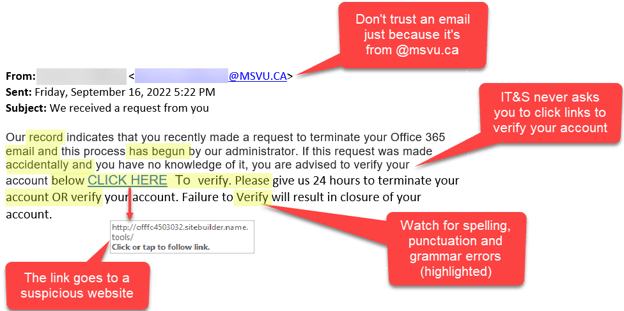
1. Email phishing
This is where attackers send emails with attachments that, when opened, inject malware into the system. Or, these emails obtain malicious links that take the victim to a site where they’re tricked into revealing sensitive data.
Before opening an email, consider a few things. Is this an unsolicited email? Is this from a trusted source? Are there any typos? Does the company have its own domain email address? Lastly, does anything look or feel off about the email?
2. Spear-phishing
This is where attackers send emails to specific targets who have information they need, such as those in sales or accounting departments. Spear-phishing attacks are mostly delivered using email.
Attackers will use a targeting approach, which means these emails will contain specifics about you, such as your name, title, hometown, or bank information, which is intended to add supposed credibility to the email. This works to the attackers’ benefit because it makes the email seem real.
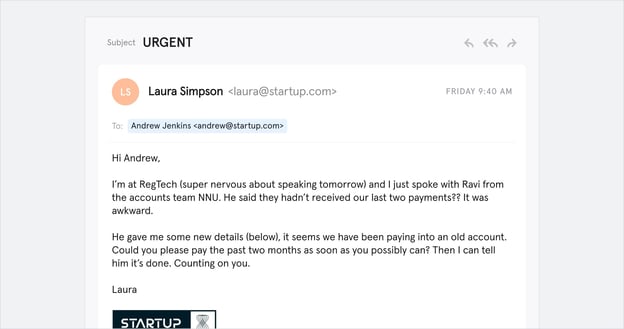
Image: https://www.tessian.com/blog/phishing-vs-spear-phishing/
3. Whaling
This is where attackers send emails to senior executives such as CEOs or CFOs as part of a high-profile targeting scam. Whaling attempts are similar to those of spear-phishing. These attempts are targeted and appear from a trusted source, but they are targeted to high-level executives within an organization. In other cases, whaling occurs when the attacker pretends to be a high-ranking professional in an attempt to fool employees at a company.
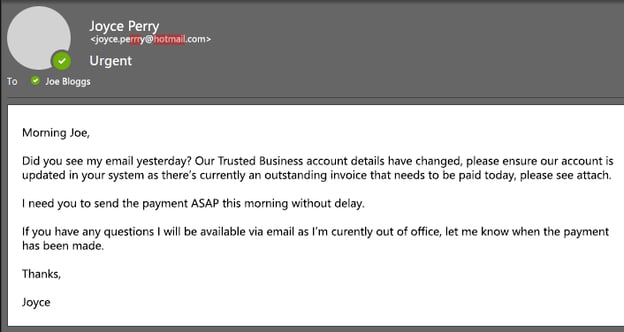
Image: https://www.aztechit.co.uk/blog/what-is-whaling-phishing
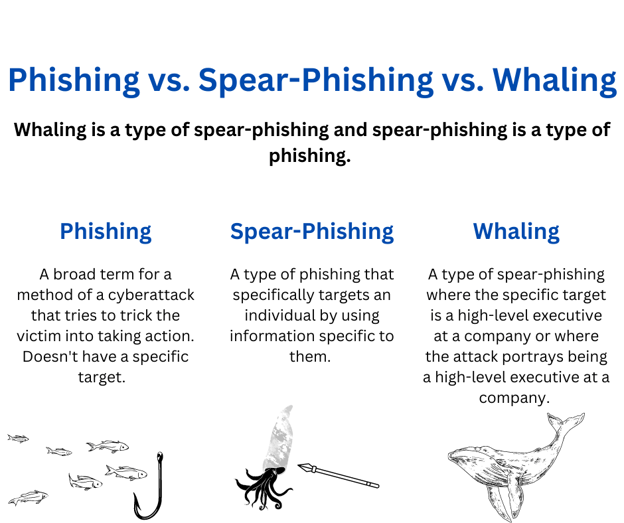
4. Smishing
This is when phishing takes place over text (SMS) messages. This occurs just as phishing, spear-phishing, and whaling do, except it takes place over text and often includes a link to a malicious website.
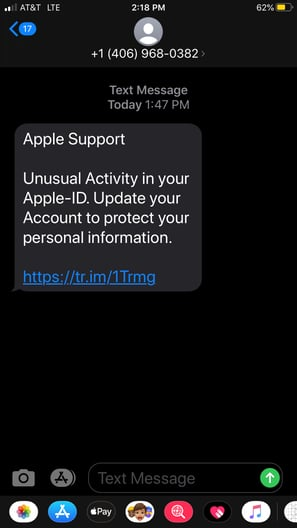
Image: https://www.secureworld.io/industry-news/5-smishing-attack-examples-everyone-should-see
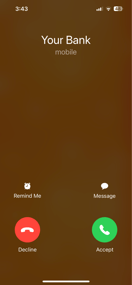
5. Vishing
Voice over IP (VoIP) and Plain Old Telephone Services (POTS) are also susceptible to phishing attacks. Attackers use speech synthesis software and automated calls to solicit victims to share personal information.
Vishing is another term for voice phishing, and it is the fraudulent practice of making phone calls or leaving voice messages impersonating reputable companies to convince individuals to reveal information such as bank details and credit card numbers.
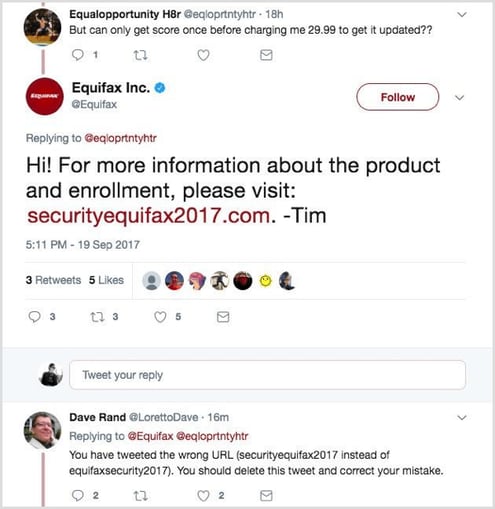
6. Social media phishing
Social media phishing occurs via social platforms such as Instagram, Twitter, Facebook, or LinkedIn – designed to take over your account or use it to post messages as part of a larger campaign. Attackers do this by creating fake login pages that prompt you to insert your personal information and passwords. This type of attack can also occur when social media accounts are hacked and post malicious links.
Image: https://www.socialmediaexaminer.com/how-to-protect-business-from-social-phishing-scam/
7. Pharming
This occurs when attackers use DNS cache poisoning (replacing a legitimate cached IP address with a malicious one) to redirect victims to fake (but similar-looking) websites where their login credentials are captured.
The difference between pharming and phishing is that phishing requires the victim to click a malicious link, while pharming takes place when your device is hacked and your information is stolen. Pharming eliminates the process of the victim clicking the link and instead skips forward to stealing your login credentials.
If you're currently experiencing a cybersecurity incident, book a crisis cybersecurity consultation. Not under duress but looking for help communicating about cybersecurity before a potential cyber attack? We can help you. Book a free cybersecurity consultation.
Photo by Mikhail Nilov
Topics: crisis communications, cybersecurity


Comment on This Article